experience &
expertise
specialists
Cyprus (HQ), Greece,
MENA, UK
experience &
expertise
specialists
Cyprus (HQ), Greece,
MENA, UK
YOUR CYBER GUARDIAN IN A CHANGING WORLD
Along with the countless opportunities the era of digital transformation and AI present, comes a fast evolving and expanding threat landscape. Threat actors move at a faster pace than organizations can react, creating a global concern over the breadth and depth of destruction cyber-attacks can cause.
With an innovative and forward-thinking mindset and a rich skillset, we have been successfully guarding our clients’ digital ecosystems for the past two decades, by helping them build cyber resilience. Through our 360 ° Holistic Approach for Achieving Cyber Resilience, we address the high volatility of the threat landscape by empowering our clients build digital ecosystems capable of anticipating, withstanding, adapting to adverse conditions, and quickly recovering from disruptive attacks.
ODYSSEY 360 HOLISTIC APPROACH FOR ACHIEVING CYBER RESILIENCE
We apply a 360° Holistic Approach in helping our clients achieve cyber resilience. Through this optimized approach, the result of our two-decade engagement in the cybersecurity arena, we enable your organization to Anticipate, Withstand, Adapt to adverse conditions, quickly Recover from disruptive cyber-threats and meet compliance obligations.
This holistic approach, consists of solutions, services and product offerings which are classified into five different Pillars. Each offering can achieve its intended purposes as part of your cybersecurity strategy, however, when carefully planned and implemented in combination, they are designed to work synergistically to enable you build resilience against emerging digital risks, in all operational aspects of your organization: People,, Process and Technology.
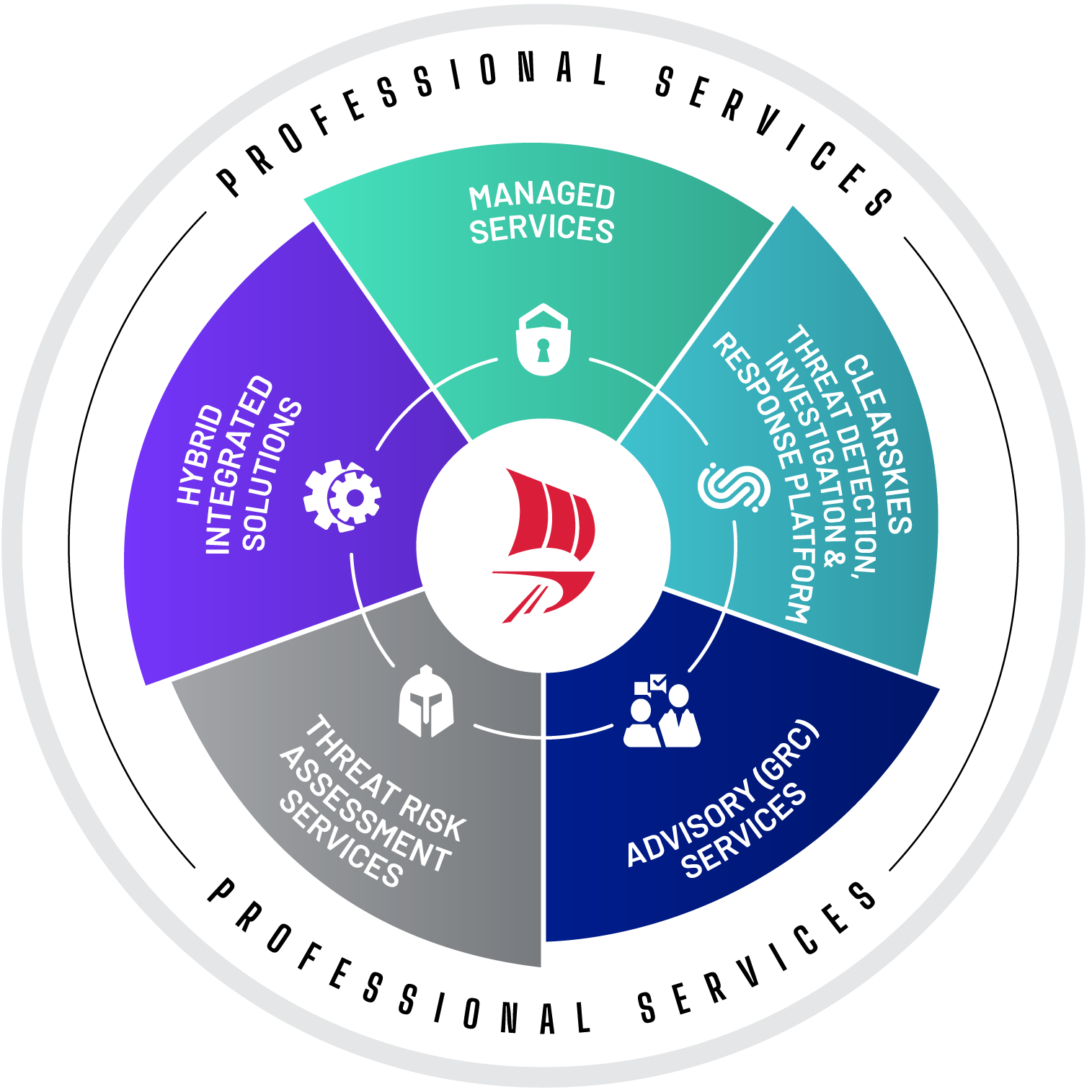
A remote extension of your organization’s Infrastructure Management, Maintenance & Security Operations.
ClearSkies TDIR PLATFORM
Minimize Attackers’ Dwell-Time, simplify the investigation process & prioritize response actions
Improve your cybersecurity posture, achieve compliance, and develop an applicable and effective cybersecurity strategy
THREAT RISK ASSESSMENT SERVICES
Identify vulnerabilities and configuration weaknesses in your digital ecosystem.
Encompass cutting-edge products, tools, and methods to enhance your organization’s Cyber Resilience in both on-premises and cloud environments.
A remote extension of your organization’s Infrastructure Management, Maintenance & Security Operations.
ClearSkies TDIR PLATFORM
Minimize Attackers’ Dwell-Time, simplify the investigation process & prioritize response actions
Improve your cybersecurity posture, achieve compliance, and develop an applicable and effective cybersecurity strategy
THREAT RISK ASSESSMENT SERVICES
Identify vulnerabilities and configuration weaknesses in your digital ecosystem.
Encompass cutting-edge products, tools, and methods to enhance your organization’s Cyber Resilience in both on-premises and cloud environments
WHAT OUR CLIENTS SAY
Odyssey’s product, ClearSkies™ gives our Board a comprehensive bird’s-eye view, with drilldown capabilities, of what is happening in our digital environment at all times.
We significantly improve the speed at which we detect and respond to suspicious behaviors inside and outside of our networks.
We have improved our strategic decision-making due to the crucial security context found in the information ClearSkies provides.
Odyssey’s product, ClearSkies™ gives our Board a comprehensive bird’s-eye view, with drilldown capabilities, of what is happening in our digital environment at all times.
We significantly improve the speed at which we detect and respond to suspicious behaviors inside and outside of our networks.
We have improved our strategic decision-making due to the crucial security context found in the information ClearSkies provides.
LATEST INSIGHTS


THREAT-ALERTS
Injection vulnerability in the Palo Alto’s GlobalProtect SSLVPN implementation
BROCHURE
MANAGED SERVICES
BROCHURE
ODYSSEY COMPANY PROFILE
Securing your Cyber Resilient Future is ingrained in our DNA. […]
EVENT
Odyssey as a Gold Sponsor in the 14th Infocom Security 2024


